BPDU Filter vs BPDU Guard
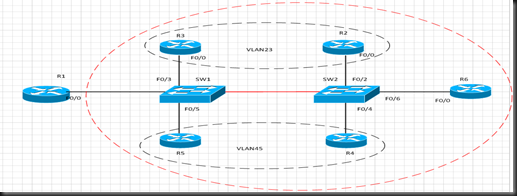
Today we will try to explore the difference between these 2 options, BPDU guard and BPDU filter We know that BPDU are used to communicate between switches in L2 networks to ensure loop free topology. BPDU Guard is used to protect our access (or trunks incase of servers) ports from receiving undesired BPDU packets, this feature is helpful in enforcing your network boundary in access layer BPDU Guard can be enabled on global configuration as well as under the interface configuration BPDU Filter on the other hand is used to filter BPDU packets outbound when configured in global configuration (after sending 11 BPDU out ) and will filter BPDU inbound/outbound when configured under the interface level To better understand these two features, let’s use this simple topology R1 is connected to SW1 through F0/0 to have R1 send and receive BPDU we will simple configure bridging group 1 on the router and we will join the bridge group when desired to test our configuration BPDU